TCA 2.1 What's new - AD authentication
Overview
Telco Cloud Automation 2.1 was released last week and this post will explore the newly introduced feature to directly access Active Directoy authentication via the TCA Manager.
Release Notes description
The release notes cover this topic in a rather brief statement:
1Integration with external Active Directory system for user authentication, in addition to vCenter Server authentication.
I will concentrate on the configuration for the virtual machine form factor of Telco Cloud Automation here, but the steps on how to configure this functionality within the Cloud Native deployment of Telco Cloud Automation can be found in the installation guide, you are looking to modify the "tcaMgr" section accordingly. TCA 2.1 Deployment Guide
Current limitations and caveats
Be warned, that once you have decided for an authentication model for the TCA Manager in the Cloud Native deployment there is no supported way of changing this today. This change is possible in the VM based deployment (though you do lose all assigned permissions when you do so).
The current implementation will allow you to utilize logins directly against an Active Directory LDAP structure for the TCA Manager only, the TCA-CPs will still be integrated with the vSphere PSC based authentication.
Only a single Active Directory backend is supported at this point in time, and since this is using an LDAP binding user iterations over trusted domains will not work, very similar to how LDAP based identity sources on vSphere work today.
Only Active Directory has been officially tested so far, which means while other schema compliant identity sources may work they are deemed unsupported.
Setup procedure
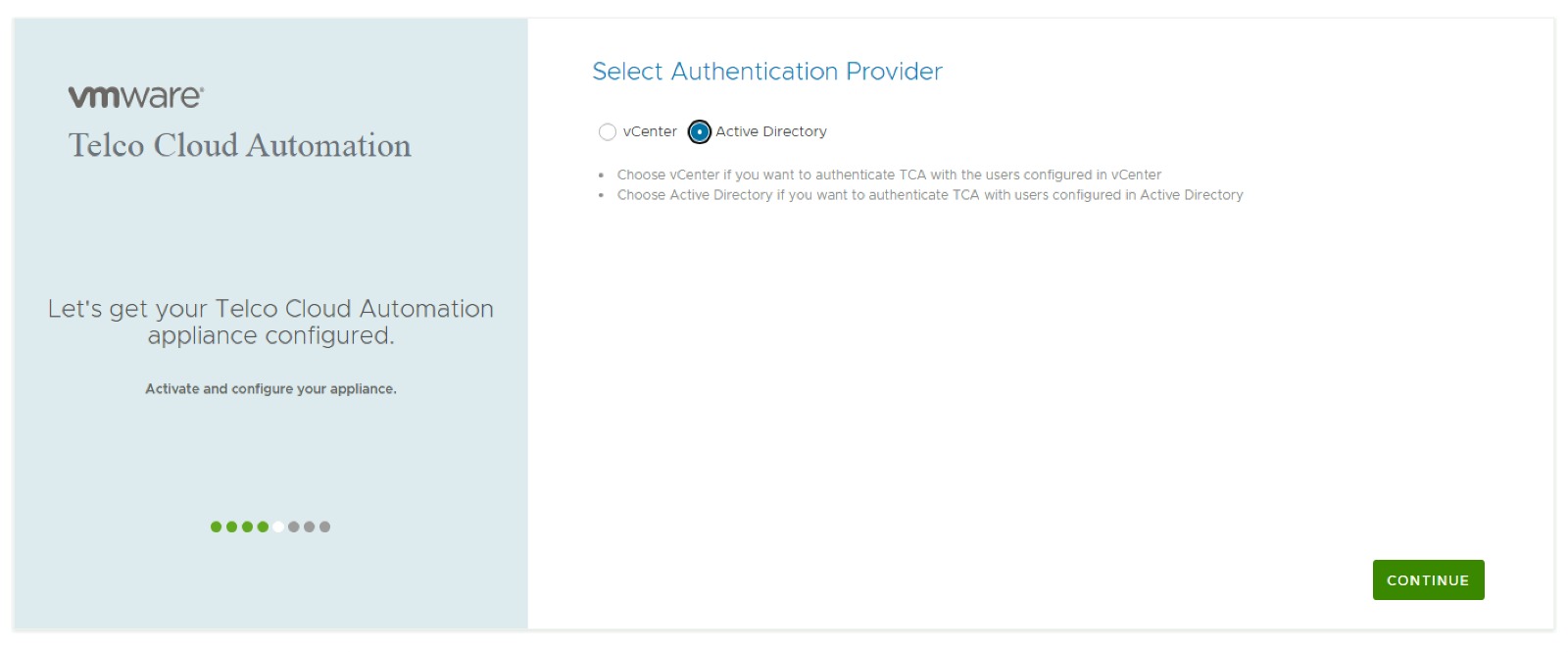
The setup procedure itself is rather simple and can be performed as part of the setup wizard for the TCA Manager. The first step is to select the Active Directory option as the Authentication Provider.
Next you provide the information required to connect to the Active Directory server, note that the Admin User Distinguished name is slightly awkwardly named, it's the LDAP bind user and only requires read-only permissions and not administrative level perissions on Active Directory.
The Admin Group name is the DN of the group of users which gain default administrative into the TCA Manager.
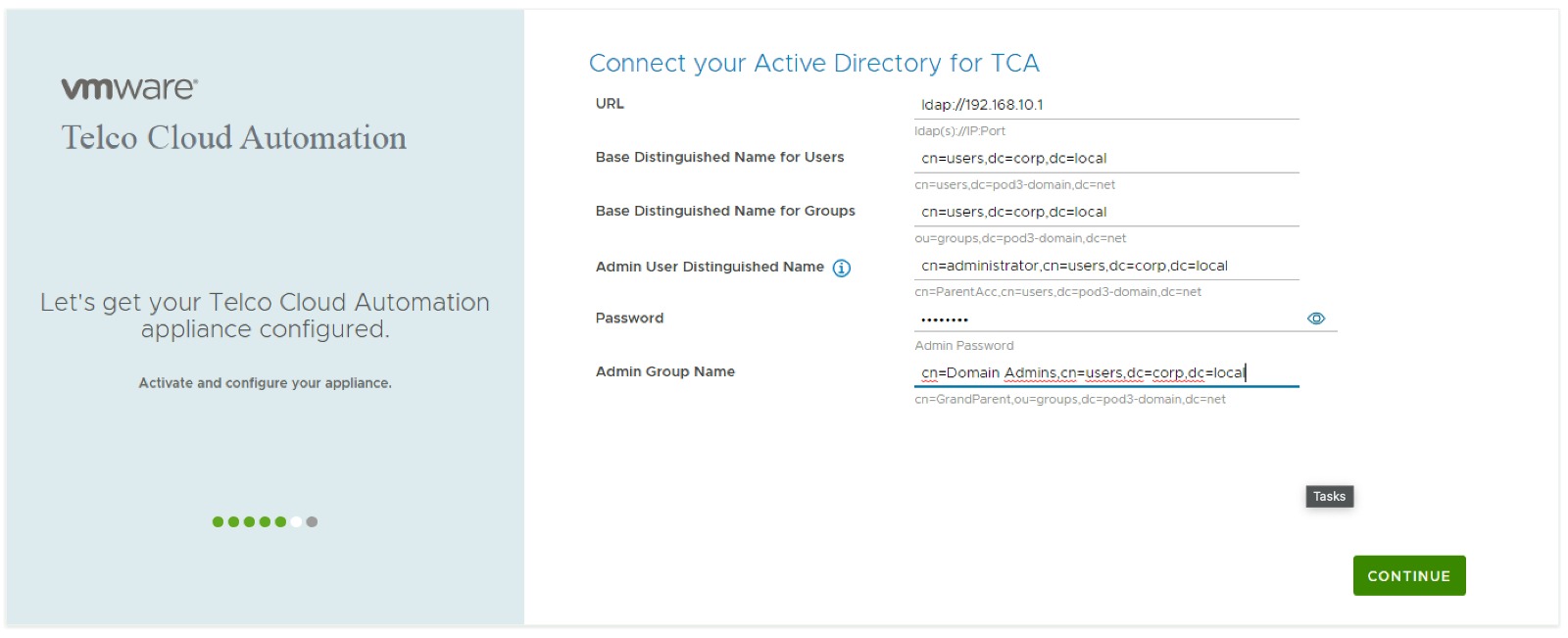
This pretty much completes the setup steps required. These settings can be modified if necessary in the appliance administrative interface at a later point in time (only in the VM based deployment)
How to login into the TCA Manager
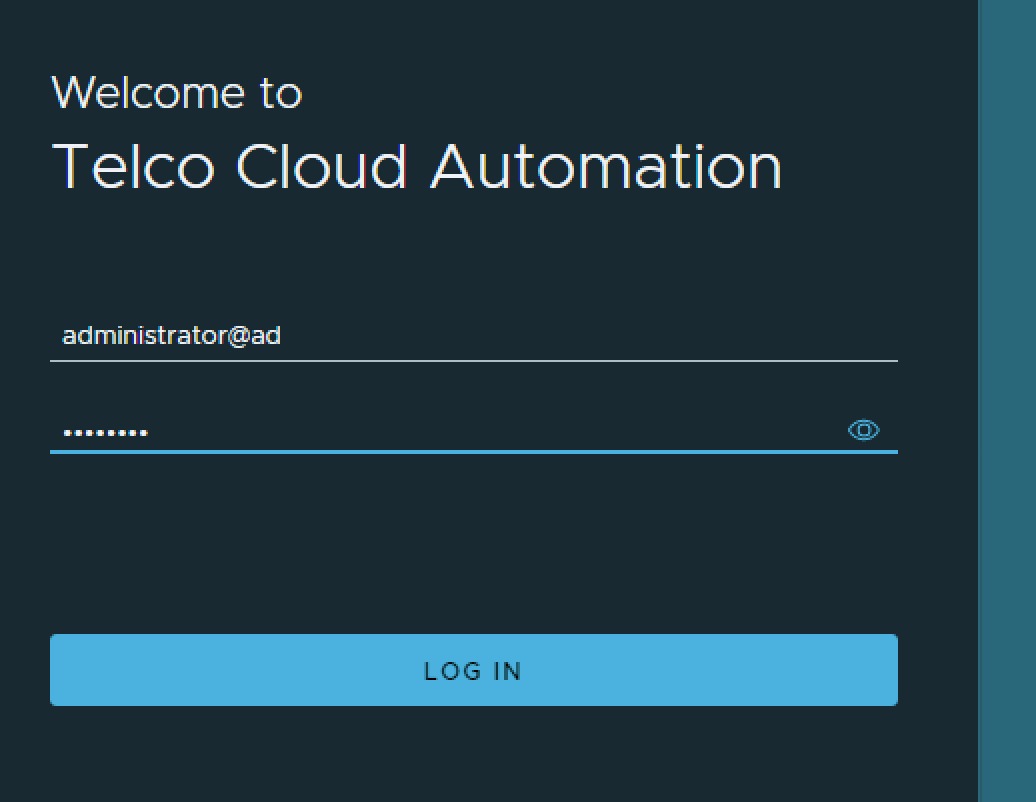
You might think that from here on you know how to actually log into the TCA Manager and this shouldn't require further elaboration. However, there is a login convention to be aware of.
You do not log in with your email address or canonical name as given in Active Directory with an account but rather in the format of username@ad, so for the user administrator@corp.local which I am using in the below screenshot this turns into administrator@ad.
I will be going over some other new features of Telco Cloud Automation 2.1 in future posts, as there is some very nice "Quality of life" improvements in this release, e.g. Kubernetes Stretched Cluster support or the possibility to now deploy specific TKG extensions directly via TCA.